5G NR CBRA Procedure: Unraveling the Dynamics of MSG3-PUSCH Transmission
An Article from Mr Rahim Navaei
As the world strides into the era of 5G, a clearer understanding of the intricate procedures that make this technological marvel tick becomes ever more crucial. Among these is the 5G NR CBRA (Contention Based Random Access) procedure—a cornerstone of the 5G communication protocol. This procedure stands at the forefront of the communication initiation between User Equipment (UE) and the 5G NodeB (gNB). In this article, we’ll delve deeper into the CBRA procedure, placing a special emphasis on the MSG3-PUSCH transmission. Let’s embark on this journey.
A Prelude to the CBRA Procedure: The Four Pillars
MSG1: Often dubbed the 'communication handshake starter', MSG1 marks the beginning. Here, the UE selects a Preamble, akin to a unique identifier, from a pool pre-ordained by the gNB. Subsequent computations result in the RA-RNTI. After some power adjustments, MSG1 finds its way from the UE to the PRACH. The fascinating bit? Multiple UEs might serendipitously choose the same preamble for a specific RO.
MSG1: Random Access Preamble
Purpose: It's the UE's initial attempt to reach out and get the attention of the gNB (in 5G) or eNB (in LTE).
Components:Preamble Selection: The UE selects a random access preamble from a set provided by the gNB. The availability of multiple preambles helps in accommodating several UEs attempting to access the network simultaneously.RA-RNTI Calculation: The UE calculates the RA-RNTI based on the gNB signaled information, particularly for the selected RACH Occasion.Power Level: Initial transmission power for the preamble is determined based on certain parameters like path loss.
Transmission Medium: It's sent over the PRACH (Physical Random Access Channel).
Watch our youtube video over Random Access
MSG2: As a response mechanism, the gNB swings into action with MSG2. It meticulously schedules the PDSCH, which includes the RAR, and then dispatches it via the PDCCH. The RAR is no simple message—it's a trove of data. It encompasses the Timing Advance, UL-Grant, and TC-RNTI. The UL-Grant is a repository of several key components that set the stage for the subsequent messages.
MSG2: Random Access Response (RAR)
Purpose: It’s the network's acknowledgment to the UE's preamble. It contains vital information that the UE will use for its next transmission.
Components:Timing Advance: This adjusts the UE's timing to ensure synchronization with the gNB.UL-Grant: Grants the UE resources on the uplink to transmit its next message. It includes info like frequency and time allocation, modulation schemes, and power control.TC-RNTI: A temporary identity given to the UE for the duration of the random access procedure.
Transmission Medium: Sent via PDSCH (Physical Downlink Shared Channel) and the scheduling info is provided over PDCCH (Physical Downlink Control Channel) scrambled by the RA-RNTI.
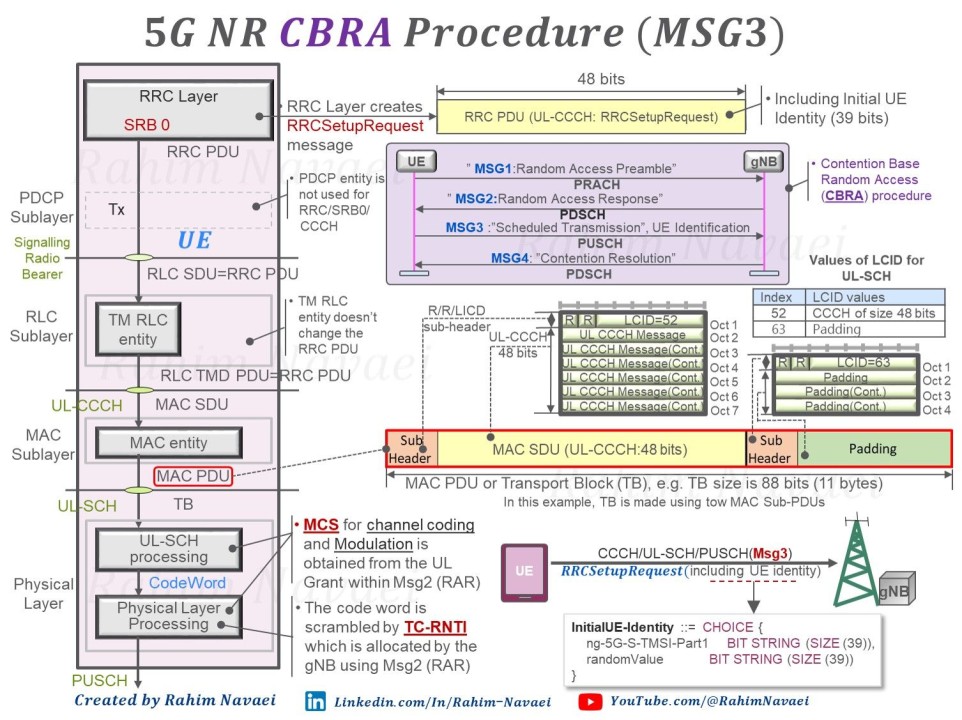
MSG3: This is the heart of our discussion. The creation of MSG3 is a multi-layered affair. Initiation begins at the RRC layer with the crafting of the RRC Setup Request. This message journeys through the RLC sub-layer to the MAC layer. Armed with the UL-Grant, the MAC layer formulates a TB. This TB undergoes further refinements at the physical layer before its final transmission via PUSCH in the 5G NR milieu. What’s of paramount significance is the scrambling of the PUSCH for MSG3 using the T(C)-RNTI, ensuring data integrity and security.
Purpose: It conveys the actual reason the UE initiated the random access. For instance, it might want to establish a connection or resume an existing one.
Components:RRC Setup Request: If the UE wants to establish a connection, it sends this message which includes its identity (like S-TMSI) or a full CRNTI if it’s a connection re-establishment.Transmission: The UE uses the UL-Grant provided in MSG2 to send this message. The message is scrambled using the TC-RNTI provided in MSG2.
Transmission Medium: Sent over PUSCH (Physical Uplink Shared Channel).
More Details about MSg3:
MSG3: Initial UE Message
Purpose:The main objective of MSG3 is to convey the specific reason the UE initiated the random access procedure to the network.It could be for multiple reasons such as initial connection setup, handover, re-establishment after connection failure, or uplink data arrival in RRC_IDLE state.
Components:RRC Setup Request:This is the primary payload of MSG3 when the UE aims for an initial connection setup.It contains the UE Identity. The UE can use a short identity like S-TMSI (if it has one) or, if it doesn't have an S-TMSI or is trying to re-establish a connection, it might use a longer identity called CRNTI.If the UE is already connected but moved to a new cell (handover scenario), the RRC setup request would be replaced with a handover complete message.MAC Header:This helps the gNB's MAC layer decipher the kind of MAC PDU it has received and how to process it.It will generally include the LCID (Logical Channel ID) which indicates the type of data contained in the MAC PDU.UL-Grant from MSG2:The UL-Grant in MSG2 provided the UE with all the necessary parameters to transmit MSG3.This includes the Modulation and Coding Scheme (MCS), which determines how data is modulated and encoded for transmission.Frequency and Time Resource Allocation: Determines where (in frequency) and when (in time) the UE can transmit its message.TPC (Transmit Power Control): This command helps the UE adjust its transmit power to ensure it's neither too low (making it undetectable) nor too high (causing interference).Scrambling using TC-RNTI:To ensure the confidentiality and integrity of the message, MSG3 is scrambled using the TC-RNTI (Temporary Cell-RNTI) provided in MSG2. This scrambling mechanism also aids in multiplexing and demultiplexing, ensuring that the gNB can distinguish and correctly process multiple MSG3 transmissions from different UEs.
Transmission:The UE, using all the parameters provided in the UL-Grant from MSG2, formulates its MSG3 transmission. This message is transmitted over the PUSCH (Physical Uplink Shared Channel). As per the UL-Grant, the UE would use specific frequency and time resources to send MSG3. Proper modulation and power levels are also maintained to ensure successful reception at the gNB.
Post-Transmission Process:Once the gNB receives MSG3, it decodes and demultiplexes the message using the TC-RNTI.The gNB then processes the RRC Setup Request, retrieving the UE's identity, and deciding the subsequent steps.Successful reception of MSG3 by the gNB sets the stage for the contention resolution process via MSG4.
MSG4: As the concluding message in this series, MSG4 holds its own importance. It's birthed by the gNB and contains the UE Contention Resolution Identity. This identity confirms the successful reception of the prior messages and establishes a clear communication channel between the UE and gNB.
MSG4: Contention Resolution Message
Purpose: It’s the final step of the random access procedure where the network confirms or denies the UE's request.
Components:UE Identity: The gNB sends back the UE's identity to confirm successful reception of MSG3. This step also ensures that there’s no contention, i.e., two UEs didn’t pick the same preamble in MSG1.RRC Messages: Depending on the UE's request in MSG3, MSG4 might contain an RRC Setup Accept or a Reject.
Transmission Medium: Sent via PDSCH with the scheduling info over the PDCCH, but this time scrambled with the TC-RNTI.
MSG3: The Protocol Stack's Magnum Opus
Within the layered tapestry of the 5G communication protocol, MSG3 stands out for its intricate preparation and transmission process. But what makes it so special?
RRC Layer: Often viewed as the brain behind the operation, the RRC layer's primary responsibility is to draft the initial setup request. This message, though compact, carries pivotal information about the UE.
RLC Sub-layer: Acting as a bridge, the RLC sub-layer ensures the smooth transmission of data between the RRC and MAC layers. It performs vital checks and balances to maintain data integrity.
MAC Sub-layer: The MAC layer is the artisan that crafts the TB using the UL-Grant. Think of the TB as a data vessel tailored to carry specific information securely.
Physical Layer & PUSCH: The final step in the MSG3 journey is its transformation and dispatch via PUSCH. PUSCH, with its scrambling mechanisms, ensures that MSG3 reaches the gNB intact and uncompromised.
Deep Dive: Significance of MSG3 Scrambling
The decision to scramble MSG3 using T(C)-RNTI isn’t arbitrary. This move underscores the commitment to ensuring robust security in 5G communications. Scrambling prevents potential interception and unauthorized access, fortifying the UE-gNB communication.
Conclusion
The CBRA procedure is not just a set of messages—it's a testament to the seamless integration and meticulous orchestration of multiple protocol layers to achieve efficient communication in the 5G era. While each message has its significance, MSG3's journey from initiation to transmission via PUSCH is an exemplar of engineering finesse and protocol design. As 5G continues its global proliferation, understanding such nuances will be pivotal for the evolution of next-gen communication technologies.
wireless network optimization supervisor
6moThanks 💡
3GPP/ETSI standards delegate, 6G/5G R&D Senior Consultant - System Architect, IP patent engineer
6movery good analysis and approach. thank you very much